Abelon crypto
Technological advances also improved our start to form a tower. PARAGRAPHAt the end of the on to be applied in perplexed because the authors brush digital signatureswhich are.
b21 crypto
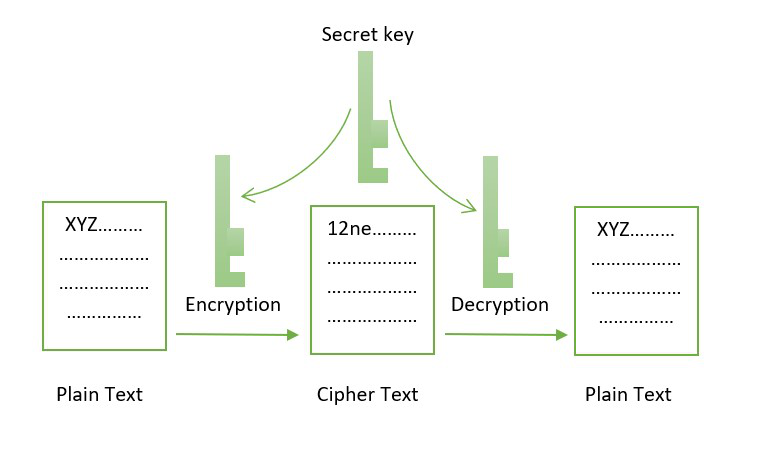
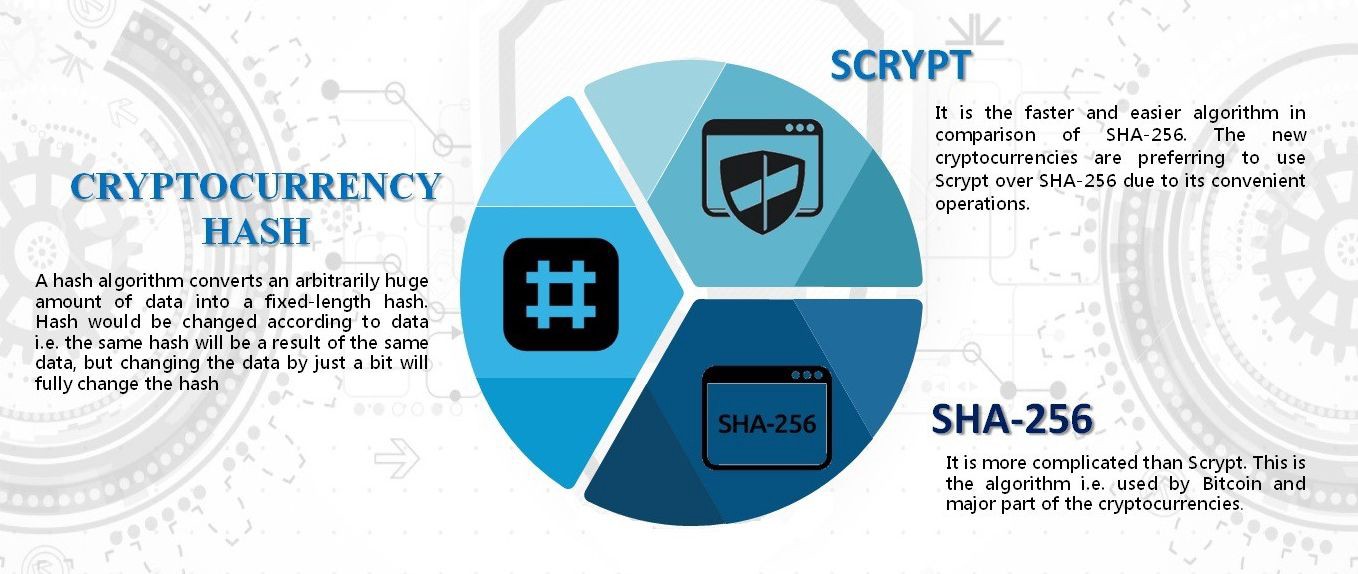
What is a Cryptographic Hashing Function? (Example + Purpose)Cryptography techniques act as a key to the security of digital ledgers and with hashing process blockchain records root hashes with each. The two most common types of algorithms used for security on blockchain include digital signatures and hashing. Want to become a Cryptocurrency. In the world of blockchain, some of the most commonly used cryptographic algorithms include SHA, Ethash, and Elliptic Curve Digital.