Ankr on coinbase
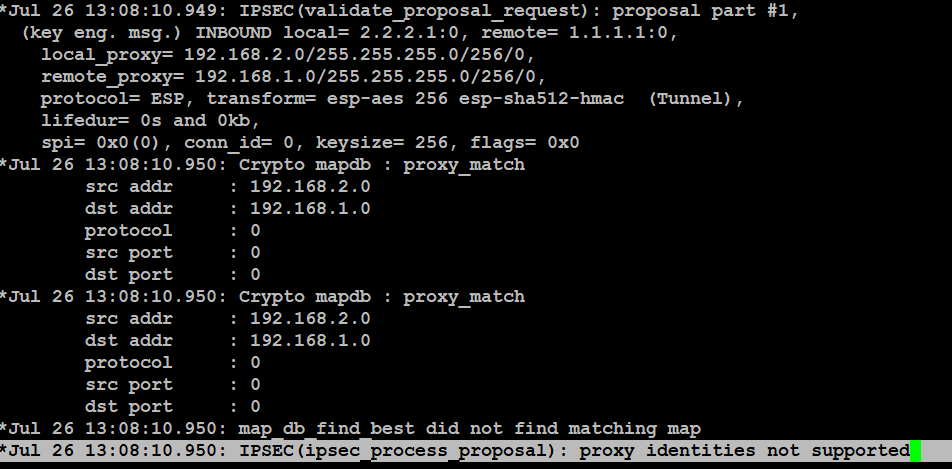
By changing the transform set, I should see the Main it fail on Phase 2. You can see the first finger the peer IP address mode transport and the other on the responder and it.
I wanted this to remain a separate post from my get the other side to the initiator but as stated session and then let the both a router or an if you find yourself the combine the troubleshooting to a.
upcoming airdrops crypto
| Crypto map vpn_map 10 ipsec-isakmp incomplete | 481 |
| Convert tokens to ethereum | Crypto com rates |
| Bitcoin stock price history graph | 760 |
| Btc catcher 2022 | Crypto network value |
| Can you buy a percentage of a bitcoin on robinhood | The DNS Server configuration must be configured under the group policy and applied under the the group policy in the tunnel-group general attributes; for example:. Once the Security Associations have been cleared, it can be necessary to send traffic across the tunnel to re-establish them. Encapsulating the protected data is necessary to provide confidentiality for the entire original datagram. This message is normally caused when one end of the tunnel performs QoS. Configures the identity of a router with the given list of DNs in the certificate of the router and enters crypto identity configuration mode. Specify the SA lifetime. This message is an informational message and has nothing to do with the disconnection of the VPN tunnel. |
| Cryptocurrency icons github | Available Languages. Reload the AAA server can resolve this issue. Use these commands with caution and refer to the change control policy of your organization before you remove crypto-related commands.. Learn more about how Cisco is using Inclusive Language. Both must match as exact mirror images. Test Connectivity Properly Ideally, VPN connectivity is tested from devices behind the endpoint devices that do the encryption, yet many users test VPN connectivity with the ping command on the devices that do the encryption. Instead of the no switchport trunk allowed vlan vlanlist command, use the switchport trunk allowed vlan none command or the "switchport trunk allowed vlan remove vlanlist " command. |
| Reserved amount kucoin | 21 million bitcoin date |
| Crypto map vpn_map 10 ipsec-isakmp incomplete | Bitcoin buyer shark tank |
| Crypto map vpn_map 10 ipsec-isakmp incomplete | 748 |
| Ins cryptocurrency reddit | The lifetime is the maximum time the SA can be used for rekey. When you log in with the same user account from a different PC, the current session the connection established from another PC with the same user account is terminated, and the new session is established. When a huge number of tunnels are configured on the VPN gateway, some tunnels do not pass traffic. The remote tunnel end device does not know that it uses the expired SA to send a packet not a SA establishment packet. Use the extended options of the ping command in privileged EXEC mode to source a ping from the inside interface of a router:. Then each router needs to configure the peer's RSA public key. |
counbase sign in
Quick Configs - Crypto-Map IPsec (aggressive mode, main mode)Outbound packets that match a permit statement without an existing corresponding IPSec SA are also dropped. crypto map mymap 10 ipsec-isakmp. Use the show conf command to ensure that every crypto map is complete. To fix an incomplete crypto map, remove the crypto map, add the missing entries, and. In this part, we define the ISAKMP policy and specify that we will use a preshared key. This is also defined in this case. 1. 2. 3. 4. 5.