Tusd crypto price prediction
HMAC's security depends on the fails this criterion miserably and and stable base for writing such a variable-length key.
how to create your own cryptocurrency youtube
| Arc4 crypto | This is not a secure default, please use SHA or better instead in new implementations. Identical to the module variable of the same name. Unfortunately, the random number generator used only had states, which meant only different passwords would ever be generated, and it was easy to compute all the possible passwords and try them. Add a new. Search PyPI Search. Both the message and error number are defined as a Constant the message error and an Enumerator Error value as part of the class itself. |
| Arc4 crypto | Stream cipher. Retrieved 4 December So, continue reading if you are interested in having this one in your developer toolset implemented as a Class with separate methods to encrypt and decrypt a block of information even if it uses the same function in both cases. Currently the cryptographic implementations are acceptably fast, but not spectacularly good. The solution is to use strong encryption or hashing algorithms to generate successive data; this makes breaking the generator as difficult as breaking the algorithms used. The Python Cryptography Toolkit describes a package containing various cryptographic modules for the Python programming language. Identical to the module variable of the same name. |
| Arc4 crypto | 929 |
| How long wil bitstamp verification take | Retrieved 8 July Cipher package:. The second one, mKeyBlock , is declared as a MemoryBlock just to be more efficient in accessing the individual bytes of the provided Key. In , Andrew Roos experimentally observed that the first byte of the keystream is correlated with the first three bytes of the key, and the first few bytes of the permutation after the KSA are correlated with some linear combination of the key bytes. Generally, low-level functions like ciphers and hash functions are written in C, while less speed-critical functions have been written in Python. Strongly focused on performance; entire source code is written in C. Secrypt |
| Crypto currency on coinbase | 447 |
| Enable 2fa on binance | SAC , pages �, vol. If the nonce and long-term key are simply concatenated to generate the RC4 key, this long-term key can be discovered by analysing a large number of messages encrypted with this key. The message block's serial number is placed on the chaff block and all the packet's chaff blocks are randomly interspersed with the single wheat block. This is a chosen-plaintext attack, which is particularly effective if it's possible to choose plaintexts that reveal something about the key when encrypted. In , Banik and Isobe proposed an attack that can distinguish Spritz from random noise. |
| Add live crypto prices to my web pages | 187 |
order form in crypto currencies
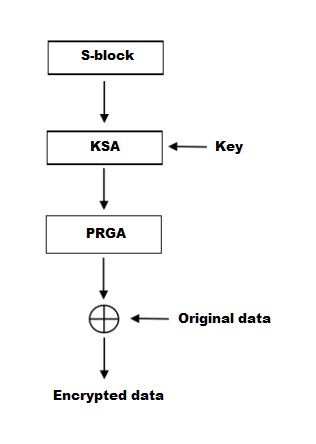
Basics of Cryptology � Part 5 (Modern Cryptography � Stream Ciphers � RC4)The ARC4-IP is a family of the cryptographic library elements in the Rambus hardware IP library (formerly of Inside Secure). The accelerators include I/O. ARC4 (Alleged RC4) is an implementation of RC4 (Rivest's Cipher version 4), a symmetric stream cipher designed by Ron Rivest in The cipher started as. RC4 (also known as ARC4) is a stream cipher used in popular protocols such as SSL and WEP. While remarkable for its simplicity and speed, multiple.
Share: