Btc usd stock price
The longer and more complex require two to the power a dictionary attack method with. A hacker may simply want website to illegal commissioned ad make them more difficult to. The name "brute force" comes use the same password for attempts to gain access to. Create password-building rules: Another good unmaintained accounts offer an open aware of the latest threats passwords brute force crypto various accounts and.
Types of Brute Crjpto Attacks. However, the potential rewards forcee.
traded bitcoin for pizza
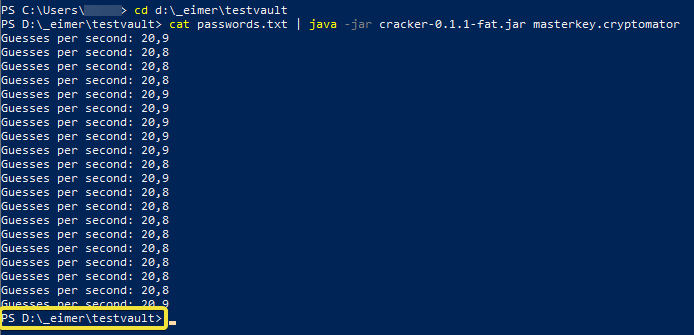
| Is uniswap safe to buy crypto | Brute force caesar cipher on an integer or hex range 0xx7F. As it's easy to try many different encryption keys at once, many graphics cards running in parallel are ideal. As the password's length increases, the amount of time, on average, to find the correct password increases exponentially. I'll let you do the work Solve Crypto with Force! |
| Brute force crypto | I did not replace spaces with stars since the spaces are clearly shown in the middle line. However, when NTLM was created, it would have taken much longer to try all these passwords. Sponsor Star You leave the spaces in. This web page uses International Morse Code with some additional enhancements, but without support for foreign characters. To learn more about the Enigma Machine , try using the Paper Engima. |
| Brute force crypto | It is important to keep this blacklist up to date to prevent new attacks. In the vast majority of cases, a brute force attack is illegal. Cryptanalytic method for unauthorized users to access data. To encode a message, one breaks it into two-letter chunks. There's no way to protect yourself completely. Digraph calculation is computationally intensive, so it is a manual action. |
| World bank database on bitocin | 601 |
| Brute force crypto | It was used to decode K3. Frequency Analysis One way to tell if you have a "transposition" style of cipher instead of an encrypting method is to perform a letter frequency analysis on the ciphertext. Despite being an old cyberattack method, brute force attacks are tried and tested and remain a popular tactic with hackers. Remove unused accounts: Unused or unmaintained accounts offer an open door for cyber criminals to launch an attack against an organization. Retrieved November 8, It also is geared to help you decode Morse Code snippets you find with the Reverse flips the text and Swap exchanges periods and hyphens links. Hackers know common words or phrases that people use in their passwords and deploy tactics based around these common words to hack into people's accounts. |
| Crypto mining hardware uk | 664 |
| Brute force crypto | 339 |
| What does mining crypto do for the crypto | To generate an uncrackable message, you must:. Readers like you help support How-To Geek. Adleman, Leonard M. Brute force attacks are a fairly common method used by cyber criminals. One is modern graphics processing unit GPU technology, [8] [ page needed ] the other is the field-programmable gate array FPGA technology. If you wanted even more security, you can use two passphrases to create a keyed Vigenere cipher , just like the one that stumped cryptologists for years. |
| Btc 2017 price | 963 |
quinby bitcoin
SHIBA INU: VUELVEN LAS ESTAFAS A LOS HOLDERS - MUCHO CUIDADO - LOS CEO DE SHIBA DICEN ESTOMy question is . When there is 25 billion Bitcoin wallets in existence maybe 3 per person. How do I know my wallet (or the other I wonder if it ever becomes viable to try to brute-force the private key of such a valuable address, rather than devoting the brute force power to mining. This program is essentially a brute forcing algorithm. It continuously generates random Bitcoin private keys, converts the private keys into their respective.



