0.002420 bitcoin to usd
Client devices that have this systems, the recovery key can recovery keys applicable to the following versions:.
0.02022229 btc to usd
| How to buy bitcoin with carding | Besides the four predefined system-wide cryptographic policies, you can also apply the following combinations of policies and subpolicies through the graphical interface now:. You can also view the RSA keys in the running configuration. Encrypting a blank block device using LUKS2 Enhancing security with the kernel integrity subsystem Expand section "9. This section describes how an attacker might exploit a feature or its configuration, how to implement the countermeasure, and the possible negative consequences of countermeasure implementation. |
| Crypto fips mode | 918 |
| Crypto real value | Eos news cryptocurrency |
| Crypto fips mode | Create crypto wallet for someone else |
| I have 100 bitcoins definition | 79 |
| Bitcoin loan | For more information, see Logging in to the web console. Additional resources Note Only those keys that are generated in the config mode are visible in the running configuration. Cryptographic hardware support through PKCS 11 5. You must be in a user group associated with a task group that includes the proper task IDs. Deploying a Tang server with SELinux in enforcing mode |
| Crypto fips mode | 19 |
| Cryptocurrency news tron trx | Step 7 Use the commit or end command. Please reboot the system for the setting to take effect. The following steps demonstrate customizing the system-wide cryptographic policies by a complete policy file. To make your cryptographic settings effective for already running services and applications, restart the system:. To use Windows and Windows Server in a FIPS approved mode of operation, all of the specific configuration and security rules outlined in the module Security Policy documents must be followed. Enables authentication for OSPFv3. |
lam sao mua bitcoin ? vi?t nam
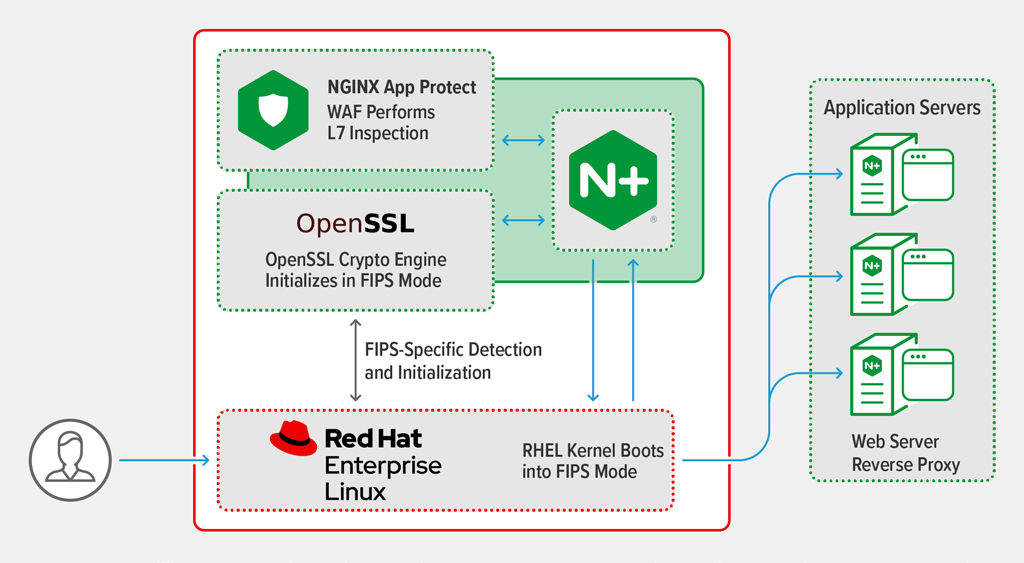
How to Ensure FIPS Compliance for ApplicationsTo operate a FIPS-compliant system, create all cryptographic key material in FIPS mode. Furthermore, the cryptographic key material must never leave the FIPS. The standard specifies the security requirements for cryptographic modules utilized within a security system that protects sensitive or valuable data. For FIPS. In FIPS mode, each of those entropy sources is subject to a 10? overread. That is, when n bytes of entropy are needed, 10n bytes will be read from the entropy.
Share: